Unraveling the Strangler Pattern (Part I): An Introduction to the Optimal Application Modernization Approach
Modernizing legacy systems is critical for unleashing flexibility and scalability in the fast-evolving digital landscape. However, the process isn’t entirely risk-free. Businesses must navigate a range of potential challenges—from service disruption to data loss—as they make the transition to the cloud. It’s no wonder why 55% of businesses struggle to determine the right approach in the early stages of modernization.
The Strangler pattern, sometimes known as the Stranger Fig pattern, is designed to mitigate the risks of overhauling an IT system. At Capstone IT Solutions, this approach has naturally become a standard for many of our application modernization clients.
Throughout this six-part series, “Unraveling the Strangler Pattern,” our experts will deepen your understanding of the Strangler pattern and its applications, as well as how you can leverage it in your own digital transformation. In this article, we’ll explore the origins, benefits, and use cases of the approach.
What Is Strangler Pattern?
The Strangler pattern is an architectural pattern used in software development that involves gradually bringing legacy systems up to date. Rather than completely rewriting critical IT systems—which can lead to costly downtime and significant operational risks—organizations incrementally replace legacy components with agile ones until cloud migration is complete.
Using the Strangler pattern is a lot like remodeling a house, one room at a time, rather than knocking the building down to start from scratch. Throughout the migration process, end users can continue utilizing the same interface as if no changes are occurring at all.
So, how is this possible? The Strangler pattern places the legacy system behind a facade. As new applications and services are added, the facade begins to reroute users to those updated versions. If a certain component hasn’t been modernized yet, the facade will simply route users to the legacy application or service. It’s a seamless process that enables old and new systems to function together until migration is complete.
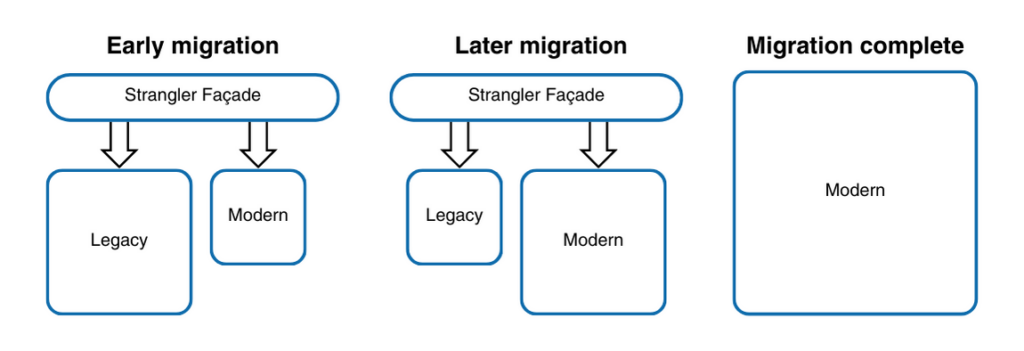
Eventually, when routing is no longer required and the legacy system is fully replaced, organizations can safely remove the facade and enjoy their modern IT environment.
The Natural Origins of the Strangler Pattern
The Strangler pattern was first introduced by software developer Martin Fowler, who discussed the novel approach in his 2002 book, “Patterns of Enterprise Application Architecture.” However, the concept of the Strangler pattern originates in nature—from the growth patterns of the strangler fig.
During a visit to Australia, Fowler noticed these massive plants in the rainforest, which would seed in the branches of trees and grow downward to root in the soil. Over time, the strangler figs would wrap around their host tree—eventually “strangling” and killing it. Interestingly, strangler figs offer protection to their host trees, while providing protection and food for animals, in the meantime.
This mirrors the architectural pattern. When leveraging the Strangler pattern, modern applications steadily take over the legacy environment, helping it function with more agility. But once refactoring is complete, the legacy system is “strangled” and fully retired.
Benefits of the Strangler Pattern
The Strangler pattern can greatly reduce the risk of application modernization. Here are three ways the approach can support your cloud migration and transformation efforts.
1. Business Continuity
While traditional, large-scale rewrites can lead to significant business disruption, the Strangler pattern enables organizations to maintain uninterrupted operations. Existing functionalities are slowly replaced with new ones—much like prioritizing a car battery replacement rather than deconstructing everything under the hood—ensuring your customers receive a continuous experience before, during, and after the migration. This not only safeguards against potential revenue losses and customer dissatisfaction, but also fosters a smoother transition within your organization.
2. Better Resource Utilization
Overhauling a complex legacy system is a hefty undertaking. In addition to adding new features, development teams must refactor every component of the old system. This requires organizations to invest a significant amount of time, money, and labor into modernization over a short period of time—or risk an error-ridden scramble as IT workers race toward deadlines.
The Strangler pattern spreads the development effort over a longer timeline. Organizations can work at their preferred pace, maintaining a sustainable budget while steadily experiencing the benefits of application modernization.
3. Minimized Risks
When legacy systems are replaced in one go, modernization can unleash a handful of risks, including undetected security issues and bugs that can compromise the health of your IT environment. On the other hand, using the Strangler pattern to make incremental updates can help you closely monitor the modernization process. Your development team can quickly resolve any issues that arise, focusing on one release at a time.
When to Leverage the Strangler Pattern
The Strangler pattern is particularly effective when robust legacy systems need to be upgraded. While companies with small IT systems may opt for an overhaul, a comprehensive rewrite may be highly impractical and vulnerable to risks for complex environments. The Strangler pattern allows businesses to break down large, monolithic systems into more manageable, independently deployable applications and services.
The Strangler pattern can also support the adoption of microservices and the integration of new features into existing platforms. It offers a flexible framework for seamlessly incorporating innovations—enhancing scalability and agility without causing upheaval. Organizations can evolve their platforms iteratively, responding swiftly to changing market demands while maintaining the stability and reliability of their operations.
In essence, the Strangler Pattern offers a versatile solution for navigating the complexities of modernization with ease. Stay tuned as we dive into the planning and implementation process for Strangler pattern implementation.