Unraveling the Strangler Pattern (Part IV): Advanced Strategies for Implementation
Successful Strangler pattern implementation invariably requires the completion of a few foundational steps—from a thorough application modernization assessment to the installation and configuration of a proxy server. However, many legacy systems are littered with complex dependencies that introduce unique challenges to the migration process.
Thus far, our six-part series on the Strangler Fig pattern has covered the initial requirements of implementation in three parts:
- An Introduction to the Optimal Application Modernization Approach
- 3 Phases of Planning and Analysis
- Key Strategies for the First Stage of Migration
In this article, we dive deeper into beneficial strategies for more intricate transitions, including data synchronization and security management.
Managing Data Migration
The Strangler pattern can help companies maintain business continuity during the modernization process. However, incremental application updates require both the outdated and updated systems to remain operational at once. Data consistency between these two environments is crucial to operational stability and customer trust.
Effective data synchronization techniques like log-based change data capture (CDC) address this need. This approach uses a CDC tool like Debezium to record all changes to one system’s database—including inserts, updates, and deletions—on a transaction log in real time. The new system instantly captures changes straight from the log, without needing to scan the source database, improving resource efficiency and accuracy.
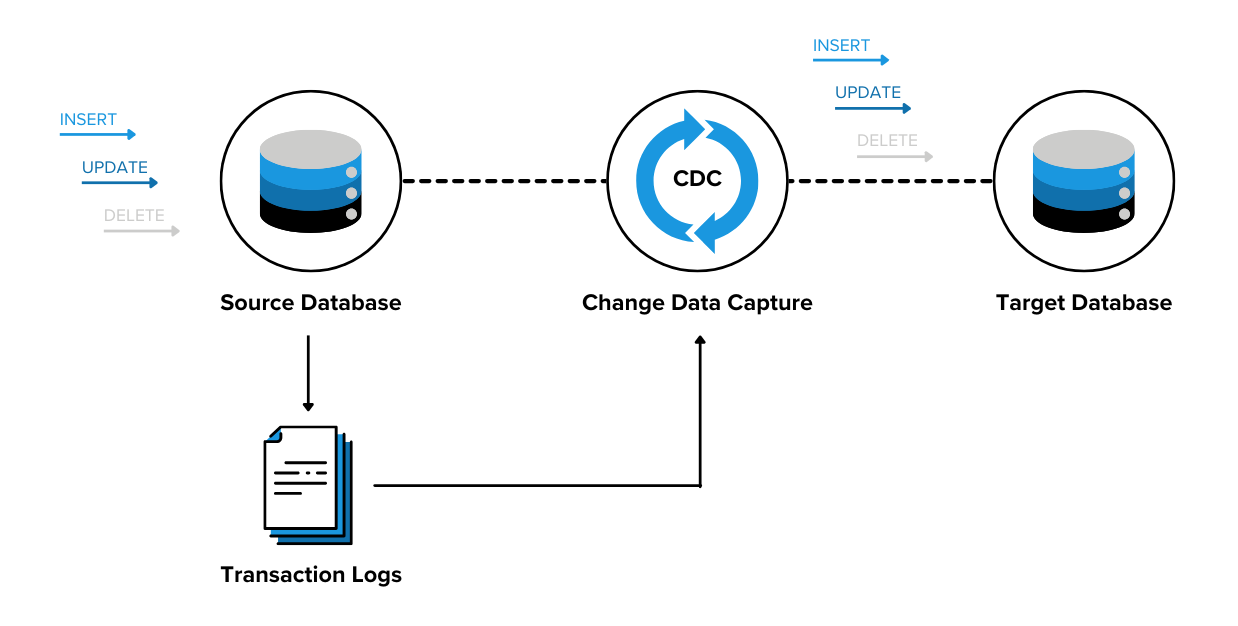
If you’re working with a particularly messy database, you can also leverage a data reconciliation tool like OpenRefine to standardize formatting, eliminate duplicate entries, and otherwise fix inconsistencies. Even if you don’t need reconciliation, routine data quality checks are critical for a smooth cloud migration.
Navigating Complex Integrations and Dependencies
In addition to data migration issues, modernization projects are often held back by the complex web of dependencies and integrations within legacy systems. Mapping out these dependencies—which can be achieved with assistance from automated tools like SolarWinds and Device42—is key to preventing data loss and downtime during transition. Dependency mapping can also help organizations identify opportunities for decomposition.
Of course, breaking down a complex legacy system requires prioritization. Many businesses start with low-hanging fruit—components with minimal dependencies that are easily isolated and moved to the new system without disrupting the original environment.
When tightly coupled components can’t be avoided, version pinning is an optimal strategy. This approach allows developers to properly test an application and its dependencies—ensuring their compatibility in the cloud—before finalizing an upgrade. Rollbacks are simple if issues occur, and catastrophic failures become far less likely to occur.
For applications with external integrations, checksum and signature verifications add an extra layer of security. This strategy prevents compromised dependencies from moving forward during Strangler Fig pattern implementation.
Maintaining Security During Strangler Fig Pattern Implementation
No migration is completely free of risk. While modernization will ultimately strengthen cybersecurity, the facade central to the Strangler Fig pattern approach can introduce vulnerabilities. The integration points and middleware between the new and existing systems become potential targets for attackers.
API gateway throttling can be an impactful security measure. By limiting the traffic to the API during a set timeframe, this method ensures it doesn’t get overwhelmed by requests. Cybercriminals cannot access either system through denial of service (DoS) attacks.
Ongoing vulnerability scanning is also beneficial to the security of your migration. Automated tools can detect security flaws and misconfigurations that leave the systems exposed—and even alert you of suspicious behavior before it escalates into a major threat. Vulnerability scanning minimizes human error and empowers developers to proactively address potential security issues.
Enveloping all security strategies should be a broad zero-trust architecture that assumes no user or system—whether internal or external—is inherently trustworthy. This approach requires strict identity verification and access controls for every user, device, and application, holistically securing the new and existing systems for Strangler pattern success.
Overcoming Strangler Fig Pattern Challenges with Expert Support
Every Strangler pattern implementation comes with unique dependencies, data migration needs, and other complexities. Identifying the right approach to address each one is essential to achieving a streamlined migration and secure digital infrastructure. With support from application modernization experts like Capstone IT Solutions, your team can gain highly tailored strategies that prevent migration issues and future-proof your new system.
Stay tuned for the next article in our series, which will examine successful examples of Strangler Fig pattern implementation, highlighting how key challenges were overcome.